The Dodeca Excel Add-In for Essbase is a VSTO (Visual Studio Tools for Office) deployment, which must be signed with a code-signing certificate in order to be installed on an end-user machine. Signing of the VSTO deployment is accomplished via the ClickOnce Prep Utility, which is provided as part of the the Dodeca Framework.
When generating the Dodeca Excel Add-In deployment package, the certificate used to sign the deployment is governed by the following settings:
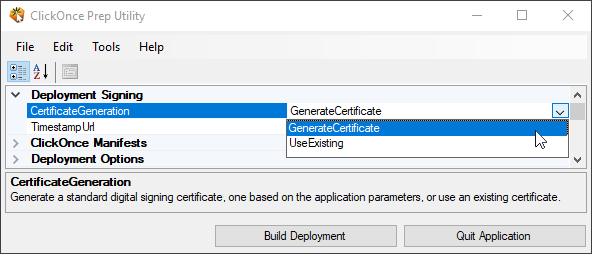
A VSTO deployment is considered fully trusted and can be installed silently
and without user interaction only when the certificate used to sign the
deployment is present in the Trusted Publishers key store and the root
certification authority (CA) is present in the Trusted Root Certification Authorities
key store. For a self-signed certificate, such as those generated by the
ClickOnce Prep Utility, this means that the generated certificate must be
present in both the Trusted Publishers and Trusted Root Certification Authorities
key stores.
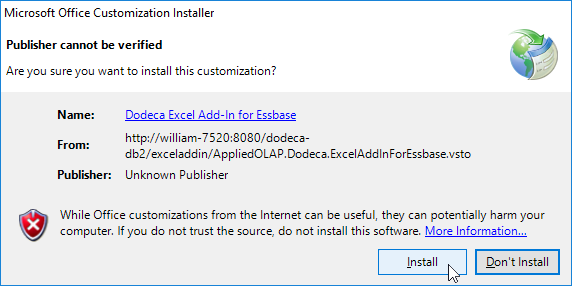
In most cases, when the deployment is not considered fully trusted, an end-user will be prompted that the publisher cannot be verified and be permitted to proceed with the installation:
In some cases, however, depending on the .NET and Office security policies utilized within an organization, the deployment may need to be fully trusted, regardless of whether user interaction to complete the installation is acceptable. In these cases, the installation will fail unless the deployment is fully trusted.
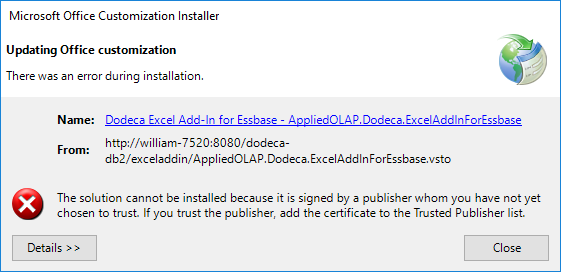
If a fully silent installation without user interaction is required, the deployment must be trusted, regardless of applied security policies.
Depending on the certificate used to sign the Dodeca Excel Add-In for Essbase
and the intended deployment mechanism, it may be required to add the certificate
to the Trusted Publishers and Trusted Root Certification Authorities
key stores under either the Current User or Local Machine scope on end-user
machines. If your organization has its own Trusted Root Certification
Authority, a trusted certificate may already be available for this purpose.
Distribution and trust of the utilized deployment signing certificate via Group Policy is the recommended approach to ensure that end-users are able to install the Dodeca Excel Add-In for Essbase without issue, regardless of the intended deployment mechanism.
See the following article for details: https://docs.microsoft.com/en-us/windows-server/identity/ad-fs/deployment/distribute-certificates-to-client-computers-by-using-group-policy
If desired, certificates can be trusted at the local machine or current user level using Microsoft’s certutil.exe, regardless of the intended deployment mechanism.
When the GenerateCertificate policy is used by the ClickOnce Prep Utility,
a self-signed certificate for each deployment URL will be generated in a
location similar to the following:
C:\Program Files\Applied OLAP\Dodeca Framework 8.1.4.35\bin
Certificates generated by the ClickOnce Prep Utility are assigned the
following password:
password
Example Local Machine Import for Generated Certificate:
certutil.exe -f -p "<password>" -importPFX Root "<cert>.pfx" certutil.exe -f -p "<password>" -importPFX TrustedPublisher "<cert>.pfx"
Example Current User Import for Generated Certificate:
certutil.exe -f -user -p "<password>" -importPFX Root "<cert>.pfx" certutil.exe -f -user -p "<password>" -importPFX TrustedPublisher "<cert>.pfx"
See the following article for further details: https://docs.microsoft.com/en-us/windows-server/administration/windows-commands/certutil
If desired, certificates can be trusted at the local machine or current user level using the Certificates snap-in for Microsoft Management Console (MMC).
See the following article for details: https://docs.microsoft.com/en-us/biztalk/adapters-and-accelerators/accelerator-rosettanet/importing-certificates-using-mmc